
Cybersecurity researchers with Qihoo 360’s NetLab today unveiled details of two recently spotted zero-day cyberattack campaigns in the wild targeting enterprise-grade networking devices manufactured by Taiwan-based DrayTek.
According to the report, at least two separate groups of hackers exploited two critical remote command injection vulnerabilities (CVE-2020-8515) affecting DrayTek Vigor enterprise switches, load-balancers, routers and VPN gateway devices to eavesdrop on network traffic and install backdoors.
The zero-day attacks started somewhere at the end of last November or at the beginning of December and are potentially still ongoing against thousands of publicly exposed DrayTek switches, Vigor 2960, 3900, 300B devices that haven’t yet been patched with the latest firmware updates released last month.
The zero-day vulnerabilities in question can be exploited by any unauthorized remote attackers to inject and execute arbitrary commands on the system, as also detailed by a separate researcher on his blog.
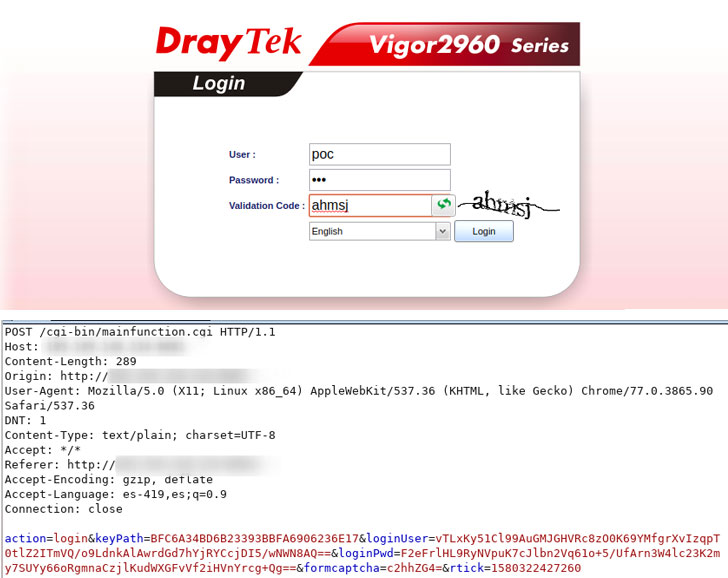
“The two 0-day vulnerability command injection points are keyPath and rtick, located in the /www/cgi-bin/mainfunction.cgi, and the corresponding Web Server program is…
http://feedproxy.google.com/~r/TheHackersNews/~3/wBKlnnST2Zo/draytek-network-hacking.html
