
Cybersecurity researchers at Reason Labs, the threat research arm of security solutions provider Reason Cybersecurity, today disclosed details of a vulnerability they recently discovered in the Facebook Messenger application for Windows.
The vulnerability, which resides in Messenger version 460.16, could allow attackers to leverage the app to potentially execute malicious files already present on a compromised system in an attempt to help malware gain persistent/extended access.
Reason Labs shared its findings with Facebook in April, after which the social media company quickly patched the flaw with the release of an updated version of Facebook Messenger for Windows users via the Microsoft store.
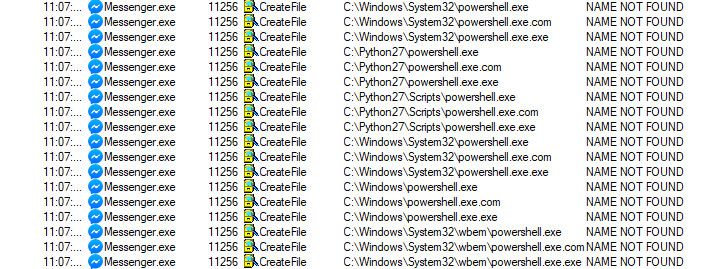
According to researchers, the vulnerable app triggers a call to load Windows Powershell from the C:python27 path. This path is typically created when installing version 2.7 of the Python and does not commonly exist in most Windows installations.
Attackers can hijack such calls that attempt to load potentially non-existent resources to covertly execute malware. Moreover, since the targeted directory is also in a low-integrity location, malicious programs could access the path without…
http://feedproxy.google.com/~r/TheHackersNews/~3/hmPQt64ByY4/facebook-malware-persistence.html
