Cybersecurity researchers today disclosed a new supply-chain attack targeting the Vietnam Government Certification Authority (VGCA) that compromised the agency’s digital signature toolkit to install a backdoor on victim systems.
Uncovered by Slovak internet security company ESET early this month, the “SignSight” attack involved modifying software installers hosted on the CA’s website (“ca.gov.vn”) to insert a spyware tool called PhantomNet or Smanager.
According to ESET’s telemetry, the breach happened from at least July 23 to August 16, 2020, with the two installers in question — “gca01-client-v2-x32-8.3.msi” and “gca01-client-v2-x64-8.3.msi” for 32-bit and 64-bit Windows systems — tampered to include the backdoor.
“The compromise of a certification authority website is a good opportunity for APT groups, since visitors are likely to have a high level of trust in a state organization responsible for digital signatures,” ESET’s Matthieu Faou said.
After the attack was reported to VGCA, the certificate authority confirmed that “they were aware of the attack before our notification and that they notified the users who downloaded the trojanized software.”
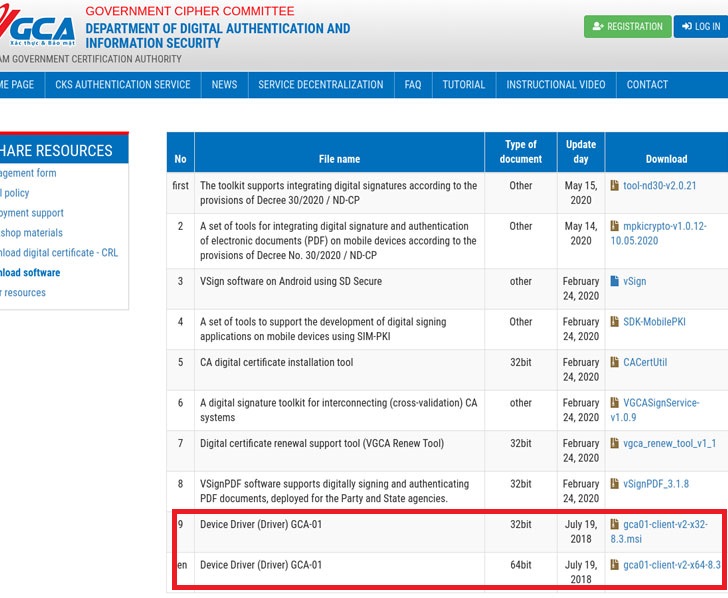
The digital…
http://feedproxy.google.com/~r/TheHackersNews/~3/BDmQJHnUqjY/software-supply-chain-attack-hits.html
