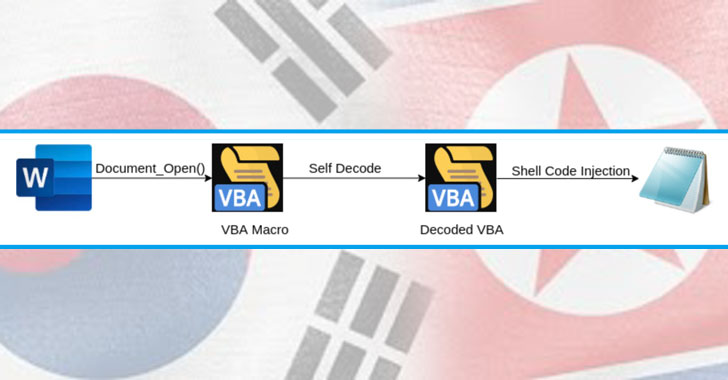
A North Korean hacking group has been found deploying the RokRat Trojan in a new spear-phishing campaign targeting the South Korean government.
Attributing the attack to APT37 (aka Starcruft, Ricochet Chollima, or Reaper), Malwarebytes said it identified a malicious document last December that, when opened, executes a macro in memory to install the aforementioned remote access tool (RAT).
“The file contains an embedded macro that uses a VBA self decoding technique to decode itself within the memory spaces of Microsoft Office without writing to the disk. It then embeds a variant of the RokRat into Notepad,” the researchers noted in a Wednesday analysis.
Believed to be active at least since 2012, the Reaper APT is known for its focus on public and private entities primarily in South Korea, such as chemicals, electronics, manufacturing, aerospace, automotive, and healthcare entities. Since then, their victimization has expanded beyond the Korean peninsula to include Japan, Vietnam, Russia, Nepal, China, India, Romania, Kuwait, and other parts of the Middle East.
While the previous attacks leveraged malware-laced Hangul Word Processor (HWP) documents, the use of self-decoding VBA…
http://feedproxy.google.com/~r/TheHackersNews/~3/yF4TY5O24po/alert-north-korean-hackers-targeting.html
