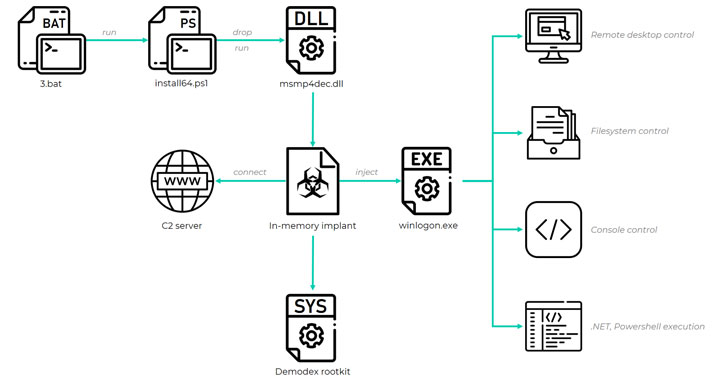
A formerly unknown Chinese-speaking threat actor has been linked to a long-standing evasive operation aimed at South East Asian targets as far back as July 2020 to deploy a kernel-mode rootkit on compromised Windows systems.
Attacks mounted by the hacking group, dubbed GhostEmperor by Kaspersky, are also said to have used a “sophisticated multi-stage malware framework” that allows for providing persistence and remote control over the targeted hosts.
The Russian cybersecurity firm called the rootkit Demodex, with infections reported across several high-profile entities in Malaysia, Thailand, Vietnam, and Indonesia, in addition to outliers located in Egypt, Ethiopia, and Afghanistan.

“[Demodex] is used to hide the user mode malware’s artefacts from investigators and security solutions, while demonstrating an interesting undocumented loading scheme involving the kernel mode component of an open-source project named Cheat Engine to bypass the Windows Driver Signature Enforcement mechanism,” Kaspersky researchers said.
GhostEmperor infections have been found to leverage multiple intrusion routes that culminate in the execution of malware in memory, chief among them being…
http://feedproxy.google.com/~r/TheHackersNews/~3/iWO3v3Txb7M/chinese-hackers-used-new-rootkit-to-spy.html
